-
IFRS
At Grant Thornton, our IFRS advisers can help you navigate the complexity of financial reporting.
-
Audit quality monitoring
Having a robust process of quality control is one of the most effective ways to guarantee we deliver high-quality services to our clients.
-
Global audit technology
We apply our global audit methodology through an integrated set of software tools known as the Voyager suite.
-
Supply Chain and Operation Services
An optimised and resilient supply chain is essential for success in an ever-evolving business landscape
-
Business risk services
The relationship between a company and its auditor has changed. Organisations must understand and manage risk and seek an appropriate balance between risk and opportunities.
-
Marketing and Client Service
We offer strategy, client service, digital and insight solutions to businesses that are shaping the future across the Middle East.
-
Forensic services
At Grant Thornton, we have a wealth of knowledge in forensic services and can support you with issues such as dispute resolution, fraud and insurance claims.
-
Deal Advisory
At Grant Thornton, we deliver deal advisory services through a strategic lens, providing end-to-end support that enables our clients to unlock value, manage risk, and make informed decisions with confidence. Our team works closely with businesses across Saudi Arabia to navigate the complexities of transactions and drive smart, sustainable outcomes.
-
Growth services
We have designed and developed growth services to support your business at each phase of its growth. So whether you are an SME that has just set up or a large business wishing to expand, at Grant Thornton we will help you unlock your potential for growth.

Senior leaders have seen significant change in the past two years in how cyber incidents are affecting their businesses. With attacks becoming increasingly sophisticated, one of the biggest challenges for companies is to measure these often intangible impacts in real terms.
In this article we speak to Adam Schrock, managing director of cyber risk at Grant Thornton US, to understand the shifting cyber landscape and mitigate against future attacks.
The changing shape of cyber attacks
With technology ever changing, there are no physical boundaries as to where and when security breaches strike. Businesses should have a robust risk management strategy closely aligned to the wider business strategy regardless of their physical location. Adam recalls the WannaCry ransomware case in May 2017, which infected and encrypted data on over 200,000 computers throughout the world.
From the UK’s National Health Service to government bodies in India, Russia, and Romania, organisations across the globe suddenly found themselves unable to access their data. The ransomware also affected universities in Canada, Indonesia and China, and numerous businesses including Honda, DeutscheBahn and LATAM airlines.
As Adam explains, WannaCry was able take control of machines because users had not installed the necessary updates to protect against known vulnerabilities that the WannaCry malware exploited. He says, “WannaCry gives us the lesson to analyse and install critical security updates on computers and mobile devices because once the malware is inside an organisation, it spreads. It is about reacting quickly and limiting the damage. Of course, where possible, it’s far better to be prepared and prevent the breach in the first place.”
Beyond the numbers
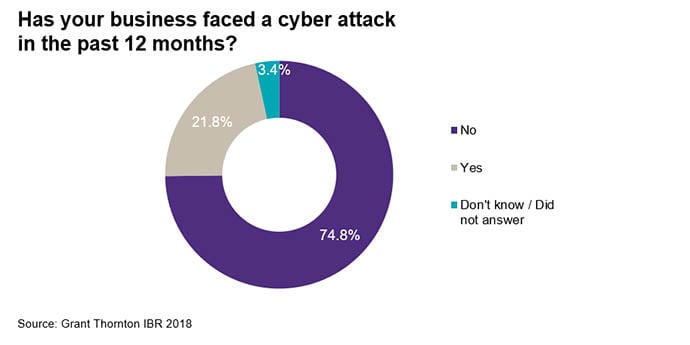
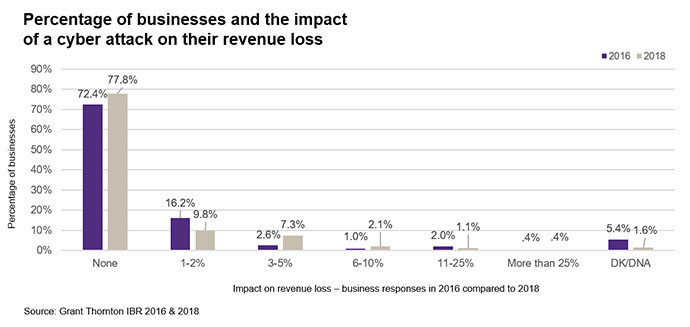
Reassuringly, the number of cyber attacks globally has not increased dramatically in the past year, though we have seen a 6.8% rise since 2015. Impact on revenue also appears stable, with businesses reporting either no loss or only a 1-2% decrease as a result of a cybersecurity breach.
However, these figures do not show us the entire picture, Adam says. “Although this increase seems low, and the general indication is the frequency of cyber incidents is stable, there is more to the story here.”
Front of mind for chief security officers and chief information officers is not only the number of cyber events affecting their businesses, but the exact impact of those breaches.
How have the impacts shifted?
The effects of cyber attacks on businesses over the past two years have significantly changed. In 2016[i], senior leaders ranked reputation loss as the most likely impact (29.2%), followed by management time (26%) and customer loss or churn (16.4%). However, senior leaders surveyed in 2018[ii] said the most likely impact had shifted to the drain on management’s time (29.9%), with reputational loss ranking second at 22.3%, and clean-up costs entering the top three position (18.4%). 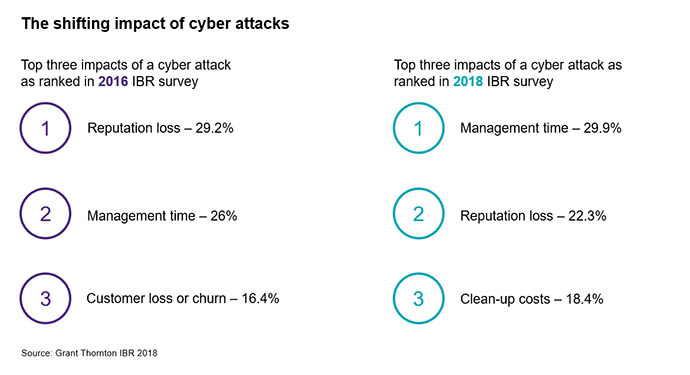
Adam sheds some light on these figures. “There’s a definite shift to the impact on board management time, technical clean-up costs and limiting the damage, be that PR, IT or otherwise.” There are many effects a cyber attack can have on a business and although the nature of a breach can vary by size and industry, there are some common themes.
“It’s important to remember that brand names and reputations are at stake immediately following an attack,” Adam says. “But for big brands, even big breaches can have a small impact in the long term.”
Home Depot is a good example – an established company with strength and infrastructure that experienced a lot of public damage following its 2014 data breach. Yet this NYSE listed company has a long-term upward trend. Despite the bumpy year or two following the data breach in 2014, Home Depot’s stock price has risen from the low US$80s in January 2014 to now fluctuating around the US$180 mark[iii]. The size of the company and its long-term growth trajectory can determine its ability to recover from an attack.
Quantifying the impact
“Ways a business can easily measure tangible impacts are by calculating the cost per record or per event.” Adam advises. “You can assign a cost of notifying people of the breach or issue you have experienced and depending on the number of customers or business partners affected, you will have a sum of the impact.”
Direct loss of sales due to the closure of a business, even for a few hours, can be calculated. Losses as a result of temporary suspension of a website, phone system or mobile app are easily discovered due to lost efficiency and being unable to take sales or enquiries. Another hard cost comes from regulatory fines.
Unfortunately, some outcomes can be less tangible, such as reputation loss or longer-term impact on revenue that is directly attributable to the attack – and the latter are much harder to assign a monetary value. Another challenge of quantifying the impact of an attack is acknowledging there is an opportunity cost of human and technical resources being taken off other projects to deal with the breach.
Other measures taken in the ‘clean-up’ may be hard to quantify, such as revenue. It is also hard to estimate loss of sales or future business as a direct result of a specific event, further complicated by any additional attacks or unrelated breaches of security.
Adam says, “What senior leaders would find useful is an effective way to measure the financial impact on a business – and this comes back to tangible and intangible measures. Brand names and reputations are at stake immediately following a cyber attack but reputation loss and integrity loss are hard to quantify.”
What action are governments taking to combat cyber attacks?
Depending on the industry and regulation environment, some governments and regulators are proactively addressing changes in the security landscape. Last August, the New York Department of Financial Services (DFS) announced[iv] a new cybersecurity regulation which requires registered financial services institutions to protect data with a cybersecurity program and to report breaches via the DFS online portal.
“Accountability is key – there needs to be a person/owner internally, be they a contractor for a specific project or a permanent staff for ongoing assessments,” Adam explains.
In Europe, the General Data Protection Regulation (GDPR) came into force on 25 May, which applies to both businesses located in the European Union (EU) and those that trade with the EU. The regulation is designed to better protect individuals and there are significant penalties for non-compliance.
Renan Piamonte, audit partner and head of risk management at Grant Thornton Philippines, adds another perspective. “As an economic bloc, the EU is in the Philippines’ top three largest trading partners for goods and services, even bigger than the United States.”
“The good news is that companies complying with the Philippines’ Data Privacy Act of 2012 have a very good chance of being ready for the GDPR, since this Act is largely based on international data privacy frameworks,” says Renan.
So, on the plus side, businesses will benefit from regulatory changes because they present an opportunity to thoroughly understand what data they hold and how to use it more effectively.
“In our experience, clients and companies in general are positive about the changes resulting from regulations such as the GDPR and have a comfort level in know they are doing the right thing,” Adam adds.
How can you protect your business from a cyber attack?
Senior leaders have different attitudes to risk depending on industry, sector and even personality type. “It is important to realise that a business can never be 100% secure,” Adam says, “and it really depends on your risk tolerance level.”
“A business can always do more to protect and prevent against risks and this is where we can help. We guide our clients on which regulations are relevant to their business and assess where they are on their maturity path. We also compare against their peers in their industry. Many clients find this valuable because we ask them where they want to be on the risk tolerance spectrum and where necessary, we help them achieve their desired security posture.”
Properly embedding cybersecurity management into existing business processes can also have huge benefits. This integration ensures that an holistic view is taken on business risks.
“We also help new CISO and CSOs when they start a new role in a business. We recommend they look at their security strategy, at regulatory compliance, and take a risk-based approach overall. Our clients like that Grant Thornton are proactive in assessing their situation. We look at gaps in their control framework and help CISOs plan for the next 3-5 year timeframe.”
What next?
If you would like to discuss your cybersecurity risk management or would like us to do an assessment of your security and control maturity level, contact our Grant Thornton team.